As the shopping season gains momentum, so do the nefarious activities of scammers seeking to exploit unsuspecting individuals. USPS text scams have become increasingly rampant, leading to serious consequences for those who fall victim. In this article, we’ll delve into the crucial need to pay attention to USPS texts and arm ourselves with knowledge to…
Identifying and Avoiding Venmo Text Scams: Protecting Your Finances and Identity
Venmo text scams have become alarmingly common, posing a serious threat to users’ financial security and personal information. The rise of these scams has led to substantial economic losses for unsuspecting victims who fall prey to the deceptive tactics employed by scammers. In this article, we explore the pervasive nature of Venmo text scams, shedding…
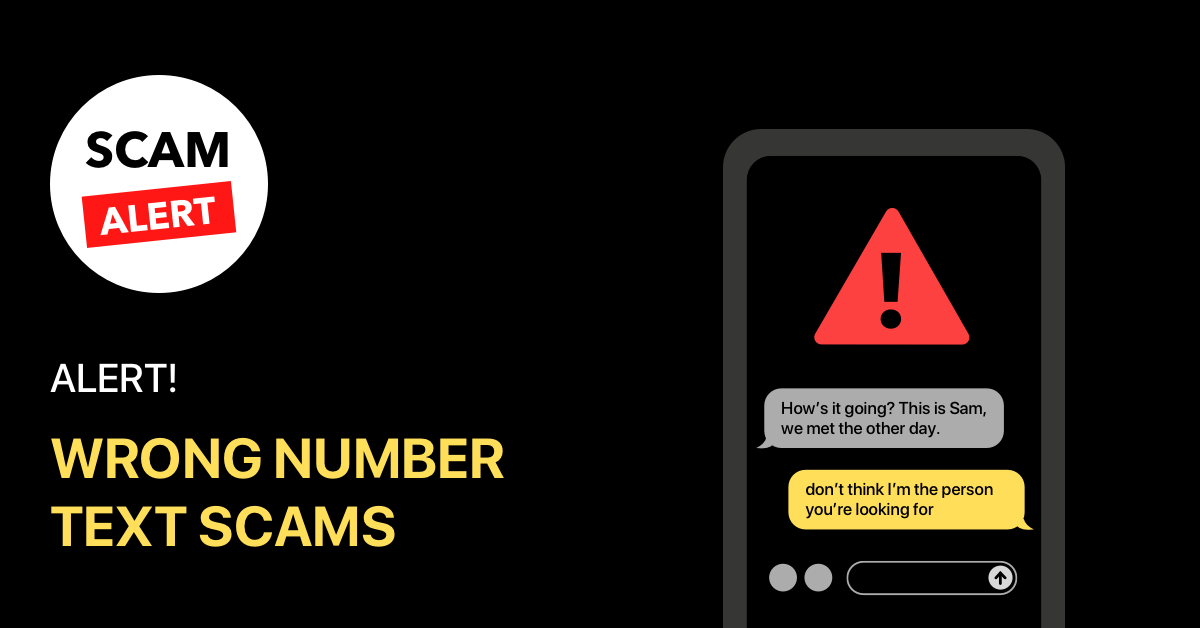
How to Spot and Avoid the Wrong Number Text Scam
Have you ever received a text from the wrong number? You may have simply dismissed it as a mistake, but you could be the target of a wrong number text scam. This kind of scam is an increasingly popular way for scammers to get personal information from unsuspecting victims. In this blog, we will discuss…
How to Block Phishing Texts: Protecting Yourself from Cyber Threats
Phishing assaults are a widespread concern for both individuals and corporations in the contemporary digital environment. Despite the fact that many people are aware of phishing emails, hackers are now focusing on utilizing text messages to deceive users and steal crucial information. Phishing texts frequently resembles straightforward communications, but if recipients fall for the trap,…
What are Scam Likely Calls and How to Block Them?
Calls marked as “Scam Likely” on our caller IDs are typical in our increasingly connected environment. These calls instantly arouse suspicion and caution. Although it’s crucial to stay attentive in defending ourselves against scams, it’s also important to realize that not every “Scam Likely” call is actually a scam. We’ll go into the definition of…
What are DoorDash Scams and How to Avoid
Many people love using DoorDash as a convenient food delivery tool when they don’t want to drive to their desired restaurant. However, lack of face-to-face interaction and data breaches, both drivers and customers have experienced different types of DoorDash scams over the past few years. So, it’s ideal to remain cautious when placing or delivering…

Buying Gift Cards? Why Do Scammers Favor Gift Cards?
Cybercriminals are always looking for ways to make quick, easy money, and gift card scams offer them a golden opportunity to use social engineering and sophisticated phishing techniques to score a payday. Many people fall for gift card scams every year. The U.S. Federal Trade Commission (FTC) says that about one in four people who report losing money to fraud…
How to Stop Spam Calls on Android
Sick of spam calls on Android? Spam calls are one of the most hated aspects of the modern age, and no one enjoys receiving them. But the truth is that we all have to deal with such calls on a daily basis. According to overall data about scam calls, there are more Android phone users…
How to Stop Robocalls on Android
A robocall is a call that delivers pre-recorded messages through auto-dialing software to millions of people each day. If you answer your phone and hear a recorded message instead of a real person speaking, you are listening to a robocall. Some robocalls provide useful information, such as appointment reminders or flight cancellations. Mostly, though, they…
Different Scam Types for Different Ages
When it comes to scamming, crooks know no age limits. Scams come in all shapes and sizes, and anyone of any age can become a victim of a fraud scheme, so it’s important to learn about them and how to protect yourself from them. While scams are most often associated with the elderly—and certainly there…



